FedRAMP® 101 – How to prepare your Cloud Infrastructure
Countless companies have been a victim of various cyber attacks which caused massive damages to them and their customers.
For companies to become prepared and more security aware, as well as have customers trust their security standard, security frameworks were introduced to create uniform standard for companies to meet and customers to depend on.
Some known compliances are:
- SOC 2 – Security standard for data management
- PCI-DSS – Security framework for Payment card industry
- ISO 27001 – establish requirements and procedures for information security management system
- FedRAMP – U.S. federal government for cloud services
What is FedRAMP:
FedRAMP framework, is a cybersecurity framework developed by the U.S. federal government to ensure the security of cloud services used by federal agencies. It is designed to provide a standard set of security controls that must be implemented and maintained by cloud service providers (CSPs) in order to meet the requirements of the Federal Risk and Authorization Management Program (FedRAMP).
The FedRAMP authorization process is complex and usually requires the assistance of a 3rd party auditor/consulting company to assist and review the system infrastructure in order to make sure it will pass the FedRAMP audit.
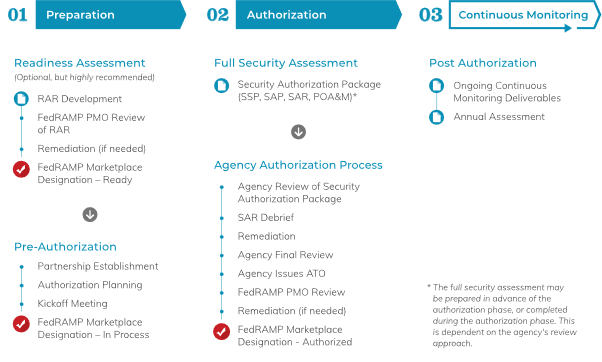
We will focus below on the technical aspects, what AWS provides out of the box and what things you need to consider as soon as possible.
Step 1: Map your architecture
FedRAMP requires that each component in your system architecture and interfaces will be checked and approved.
These include:
- External software components- Git, Slack, Cloud security and scanning products
- Architecture infrastructure – Servers and OS, Cloud Managed services
- Software products – DB software, VPN client, K8s implementation and more
Each of these components will need to be reviewed and approved by several factors as will me mentioned next.
Step 2: How to get up to standard
The framework technical specs usually focus on 4 major topics:
FedRAMP approval for cloud software and services:
This requires you to check each managed service and 3rd party SaaS platform for FedRAMP approval. You can check the authorized product list via the FedRAMP marketplace: https://marketplace.fedramp.gov/
for AWS services you have an easily accessible list mentioned here: https://aws.amazon.com/compliance/services-in-scope/FedRAMP/
FIPS 140-2 compliance
In short it requires maintaining encryptions for all components in both “in-transit” and “at-rest” states using up to date and approved encryption algorithms.
There are several levels of FIPS 140-2 and according to the FedRAMP level required you will need to comply with the matching level.
As with the FedRAMP approval you will need to make sure you are using FIPS certified modules for your software components using the following link:
Furthermore, most software vendors have dedicated guides on how to configure FIPS for their product.
For example, in Amazon Linux you can use the following guide:
https://aws.amazon.com/blogs/publicsector/enabling-fips-mode-amazon-linux-2/
CIS Configuration
CIS (Center for Internet Security) publishes security standards for various components, these are important and cover multiple requirements of the FedRAMP framework.
In our case the most relevant are OS CIS benchmark and Cloud CIS benchmark, of course additional components can also have CIS benchmarks such as: K8s, databases and more.
The full list can be found here: https://www.cisecurity.org/cis-benchmarks/
In AWS there are several services that can be implemented quickly and provide you with CIS coverage:
- Using AWS Security Hub you can activate “CIS AWS Foundation Benchmark” which will give you full cloud level coverage of your existing state.
- AWS Inspector allows CIS OS level scanning to monitor EC2 servers
- AWS Marketplace offers CIS Certified AMI to provide you with out of the box OS images to be used with all the CIS configuration already completed.
Monitoring and prevention
FedRAMP requires you to demonstrate security awareness for your architecture as well as prevention methods to protect it.
Monitoring:
- Compliance monitoring – all the above requirements including FIPS + CIS standards will need to be regularly checked and be available in a reporting format
- Security monitoring – security incident monitoring should be available for both cloud layer and application layer usually with a SIEM system
- Vulnerability scanning – you will be required to perform scheduled vulnerability scanning for all layers of your architecture
Prevention:
- Security updates should happen on a monthly/bi-monthly basis and depending on vulnerability severity level
- Anti-virus/Anti malware software will need to be applied to your servers and data
- HIPS (Host Intrusion prevention system) is recommended to include a response to zero day attacks
Summary
FedRAMP process is a long one and will probably require few major changes and even replacing existing software.
Work with a professional auditor and be prepared to focus on the above mentioned. Furthermore FedRAMP approval process and required adjustments can usually take between 1-2 years so start the process as soon as possible.
Additional info:
https://marketplace.fedramp.gov/
https://aws.amazon.com/compliance/services-in-scope/FedRAMP/
https://csrc.nist.gov/projects/cryptographic-module-validation-program/validated-modules/search?SearchMode=Basic&Vendor=amazon&CertificateStatus=Active&ValidationYear=0
https://www.cisecurity.org/cis-benchmarks/
Useful AWS Services
- AWS Config – runs compliance checks on your environment based on best practice rulesets
- AWS Security HUB – allows concentrating security monitoring status from AWS services and 3rd party tools
- AWS Inspector – scans EC2 servers and validates CIS compliance configuration
- AWS Marketplace – can be used to get pre-configured server images(AMI) for standard servers or 3rd party tools as well as software licenses.
Eran Zehavi
CTO | Lead Solution Architect

